Symantec Warns of Long-term Espionage Malware, Regin
Regin, a top-tier espionage tool that enables stealthy surveillance, was used to spy on governments, businesses, researchers and individuals since 2008, Symantec said in its official blog post today.
An advanced piece of malware, known as Regin, has been used in systematic spying campaigns against a range of international targets since at least 2008. A back door-type Trojan, Regin is a complex piece of malware whose structure displays a degree of technical competence rarely seen.
Customizable with an extensive range of capabilities depending on the target, it provides its controllers with a powerful framework for mass surveillance and has been used in spying operations against government organizations, infrastructure operators, businesses, researchers, and private individuals, Symantec said.
Regin infections have been observed in a variety of organizations between 2008 and 2011, after which it was abruptly withdrawn. A new version of the malware resurfaced from 2013 onwards. Targets include private companies, government entities and research institutes. Almost half of all infections targeted private individuals and small businesses. Attacks on telecoms companies appear to be designed to gain access to calls being routed through their infrastructure.
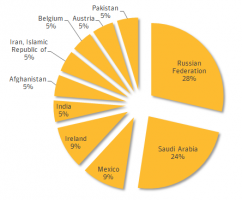
The bug has also been very active in Saudi Arabia, accounting for 24 percent of all infections. Other nations mentioned by Symantec include Mexico, Ireland, India, Afghanistan, Iran, Belgium, Austria and Pakistan.
Regin’s developers put considerable effort into making it highly inconspicuous. Its low key nature means it can potentially be used in espionage campaigns lasting several years. Even when its presence is detected, it is very difficult to ascertain what it is doing. Symantec was only able to analyze the payloads after it decrypted sample files.
It has several “stealth” features. These include anti-forensics capabilities, a custom-built encrypted virtual file system (EVFS), and alternative encryption in the form of a variant of RC5, which isn’t commonly used. Regin uses multiple sophisticated means to covertly communicate with the attacker including via ICMP/ping, embedding commands in HTTP cookies, and custom TCP and UDP protocols.













